FISA’s License to Hop
How the FISA warrant on Carter Page enabled Obama Administration surveillance of the entire Trump team, and why civil libertarians should be worried
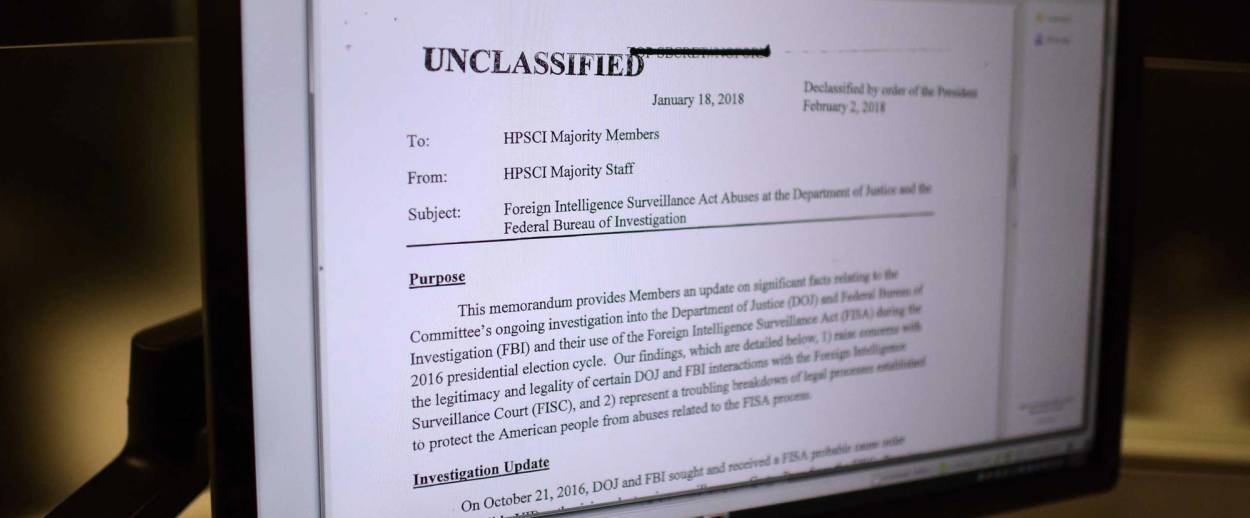



A few weeks ago, Americans learned, from a letter sent by Sen. Charles Grassley (R-Iowa) to former National Security Adviser Susan Rice, that Rice had sent herself an unusual “email for the record” on Barack Obama’s last day in office. In the email, Rice claimed to be memorializing a high-level meeting of Obama officials in January 2017, at which they discussed whether to limit the information they were sharing with President-Elect Donald Trump on the investigation of Russian interference in the 2016 election.
Former federal prosecutor Andrew C. McCarthy, writing at National Review Online, concluded that the purpose of this meeting was to keep Trump in the dark about the extent to which he himself was under investigation. He concludes from the fact of the email’s existence and its odd timing that the device of briefing Trump on limited portions of the documentation was a tactic —one intended to obscure the fact that Trump was a target of the investigation, even if he was not technically the subject of it. In fact, McCarthy wrote, given the type of investigation, Trump was effectively the main target.
In establishing this, McCarthy alluded to an aspect of counterintelligence investigations and surveillance that Americans tend to know little about. This is McCarthy’s key passage (emphasis in original):
Whether eavesdropping is done for national-security purposes under FISA [the Foreign Intelligence Surveillance Act] or for law-enforcement purposes under criminal statutes, the objective is always the same: to uncover the full scope of a conspiratorial enterprise. The point is to identify all of the conspirators, and especially to establish the complicity of the most insulated leaders. Carter Page may have been the surveillance target named in the FISA warrant, but he was of low rank in the alleged conspiracy. The point of monitoring Page was to determine exactly what he was doing and, just as crucial, who was directing him.
McCarthy’s point here means that the surveillance authorized by the FISA warrant wasn’t limited to the personal communications of Carter Page; it only began there. To understand the “conspiratorial enterprise,” investigators and analysts have to follow up on all the entities Carter Page is in contact with.
And they don’t stop there. A conspiratorial enterprise is bound to involve communications beyond Carter Page’s first circle of direct contact, so investigators need to look at the next circle as well. They may need to look further, depending on the communications patterns they find in the first two circles radiating from their named target. But under current rules, it’s the first two that government investigators can routinely gain access to in order to “uncover the full scope of a conspiratorial enterprise,” without needing to apply for further warrants.
This convention is referred to as the “two-hop” rule, and, like many provisions of surveillance law, has come in for criticism by civil libertarians. The original FISA was passed in 1978, before the internet age. After 9/11, information technology enabled surveillance operators under the Patriot Act, which complemented and in some ways overlapped FISA surveillance, to inaugurate a “three-hop” rule exploiting computer-networked communications to look well beyond the first-order contacts of a central subject (under Patriot Act surveillance, a terror suspect). This was done via presidential order and came as an unwelcome surprise to the public when the practice was revealed, and initially dubbed “warrantless wiretapping,” in 2005.
Subsequent efforts to rein in intelligence-community hopping resulted in some restrictions on the margins, but ultimately in the codification of post-9/11 practice, which was framed as aiming to prevent a terror attack on the US homeland. In 2008, with the FISA Amendments Act, Congress effectively authorized the three-hop rule used under the Patriot Act—although that point was understood by the public only in hindsight, following the revelations about surveillance practices made by National Security Agency (NSA) contract worker Edward Snowden.
Following the Snowden bombshell in 2013, the Obama administration limited routine access to a two-hop rule, which—after passage of the FISA Amendments Reauthorization Act in January 2018—is where things stand today. (The much-criticized surveillance authorization under the Patriot Act expired in 2015, although some practices were modified and continued under the USA Freedom Act.)
But the implications of the two-hop version of the “license to hop” are bigger than they appear. To understand the extent of what the FBI was empowered to do by the FISA warrant for Carter Page, we must add another factor: the type of surveillance available for exploitation, and the breadth of data involved in it.
Some of the surveillance done under “warrant” approval from the Foreign Intelligence Surveillance Court (FISC) may be current surveillance, which may entail watching a subject’s texts, emails, phone calls, etc. as they occur in real time. But a great deal of what we call “surveillance” today is actually data-mining—using the fabled NSA database—or direct requests from federal agencies for customer data stored by telecoms and internet service providers.
Analysts look at communications patterns before trying to narrow down roles and identities in a conspiracy. They don’t probe beyond “metadata” for personally identifying information at random, or on every contact they see in the array of a subject’s communications. There is a good-faith overlay of rules, analytical judgment, and supervision on the entire process.
But: The use of controls should not obscure for us the scope of what’s actually going on. Data-mining, in particular, is inherently about hunting through data that’s already there, because it is routinely collected, or stored under legal requirements and made available to the US intelligence community on demand. For some types of communications data, it is possible to retrieve information from as much as five years back in the relevant database.
In the case of a subject like Carter Page, that means investigators who obtain a warrant in October 2016 can hunt through his communications going back several years before that date—and can use their “license to hop” to probe the first and second order of correspondents linked to him at any point during that period in the same fashion. (As mentioned at links above—here and here—analysts working national-security surveillance without a targeted warrant can routinely go back for an 18-month haul.) Links from the past can then be exploited going forward.
What this means in practice is that, under a single warrant, anyone Page had a text or phone call with in the Trump campaign during the brief months of his association with it in 2016, was fair game, as a direct connection, all the way through the end of the last warrant-extension period on Page in October 2017. The second-hop connections of those initial contacts—meaning everyone that those people had contact with—are also fair game. In other words, it’s likely that almost everyone on the Trump campaign staff was included in the universe of first- and second-order contacts of Carter Page. The entirety of their correspondence is therefore also covered by the initial warrant, regardless of whether or not they ever met or corresponded with Carter Page, or whether that correspondence referred to him in any way, directly or indirectly.
We got a glimpse of that reality from the recent report that Carter Page was in contact with Trump adviser Steve Bannon in January 2017, which could have allowed the FBI to look further into Bannon’s communications through October 2017. But it also allowed a probe of Bannon’s communications going back years before January 2017—as well as a probe of anyone Bannon was in contact with throughout that same period.
Think that over for a moment, and you can see why the Carter Page warrant is important. The possible abuse of that warrant for partisan political purposes would likely be a violation not just of Page’s rights, but of the rights of thousands of other Americans—and by extension, of the right of all Americans to be free from warrantless surveillance.
A final factor, one seldom discussed, conveys the sheer scope of the hopping effectively authorized with FISA surveillance. That factor is the national-security surveillance for which no special warrant is needed because it starts with a foreign subject. The FBI, from July 2016, was conducting a counterintelligence investigation of Russian activities as they related to the election. The American public has no sense at this point of the scope of any electronic surveillance of Russians incident to that investigation—because to perform surveillance of Russian nationals for national-security purposes, the FBI doesn’t need to obtain warrants from the FISC naming those individuals. And for routinely authorized types of searches, the two-hop rule still applies.
The two-hop surveillance rule is eye-opening to many people who haven’t been aware of it. But under current law, it is not a rogue operation. From the standpoint of specific conspiracy investigations, as well as of general, ongoing surveillance of actors and networks who pose a real, physical danger to American lives—e.g., tracking the networks of foreign spies, terrorists, and drug cartels—the license to hop is an essential counterintelligence tool. The original purpose of FISA—and still the central one—is not to prevent surveillance but to enable it, while also protecting the rights of American citizens.
When communications that are reasonably believed to be those of “U.S. persons” become significant to a counterintelligence investigation, the FBI is legally subject to constraints on handling them (as are other agencies). Investigations may not require “unmasking” the identities of all entities whose communications are of interest, and if it isn’t needed, it simply shouldn’t be done. Where it is necessary to probe the identifying information of U.S. persons, the attorney general has accountability reporting requirements to the FISC (often, if not always, after the fact). Other constraints are levied by FISA and its amendments. Executive Order 12333 and its revisions govern how the intelligence agencies, including the FBI, further handle, store, and protect the data when it has been processed to the extent of unmasking U.S. persons. (Watchdog groups were notably critical of a revision to E.O. 12333 made at the very end of the Obama administration. How reliable and effective those rules have actually been since 9/11 is widely disputed.)
Being aware of the legal constraints on government surveillance of U.S. citizens and the government’s respect or lack of respect for those constraints in practice is essential for an informed and engaged citizenry. If Andrew McCarthy is right, the statements of FBI and Justice Department leaders in 2017 that Trump was not a “suspect,” or the “subject” of an investigation, were at least somewhat misleading. Given the two-hop rule, we don’t know the extent to which he and his team were actually under surveillance. But we can guess. And for the health of our republic, we should probably find out.
***
You can help support Tablet’s unique brand of Jewish journalism. Click here to donate today.
J.E. Dyer is a retired Naval Intelligence officer living in Southern California. She co-founded the blog LibertyUnyielding.com.